With billions of active users, Instagram is one of the most popular social media platforms in the world. This popularity makes it a prime target for hackers. So it is no wonder to know that “hack instagram” is a widely searched keyword across the internet. While you might see websites and iPhone / Android apps claiming to “hack Instagram,” the truth is that most of these IG hack tools are scams.
Why those “Instagram hacker” tools don’t work:
Instagram (owned by Meta) invests heavily in security. They don’t want their users to be compromised. Successful attacks usually exploit human vulnerabilities rather than technical flaws in Instagram itself. This means things like phishing and social engineering are the real threats, definitely not the Instagram password hackers available online.
Before you ask who I am to talk about Instagram hacking, let me tell you that I hacked into Instagram and got a reward of $30,000 for my finding. You can read about it here.
What we are going to see is a list of all the techniques possible to hack someone’s Instagram account and their respective prevention techniques.
Please remember that this article is written with the aim of educating people about how Instagram hacking works and how should they prevent such hacks. Therefore don’t use these techniques for malicious purposes.
1. Remote key loggers / Spyware
Remote keylogger is a piece of software that records whatever you type on your mobile or computer, including passwords and credit card details and send it to the person who installed it. Spyware is a broader term that includes keyloggers and other malicious software that monitors your activity.
Most operating systems (including android & iOS) require root access before any app could record sensitive information. That’s why rooting / jail-breaking your phone isn’t a great idea when security is concerned.
Mobile spyware is a very useful software for parents who want to monitor their kids mobile activity. There are hundreds of free and paid spyware mobile apps and remote keyloggers available on the internet. You can google it for more details.
How they spread: These often require physical access to your device to install, or they might trick you into downloading a malicious app.
How to protect yourself from mobile key loggers?
- Don’t root or jailbreak your phone: This compromises built-in security measures.
- Install reputable anti-malware/anti-spyware software: Keep this software up to date.
- Be cautious with third-party keyboards: Only install keyboards from trusted sources.
2. Phishing
Phishing is a very successful technique used by hackers to hack an account’s password. It involves creating a fake copy of a website’s login page to steal a user’s password. When a common user lands on such page, he/she might enter their username & password thinking that is legitimate login page and get their account hacked.
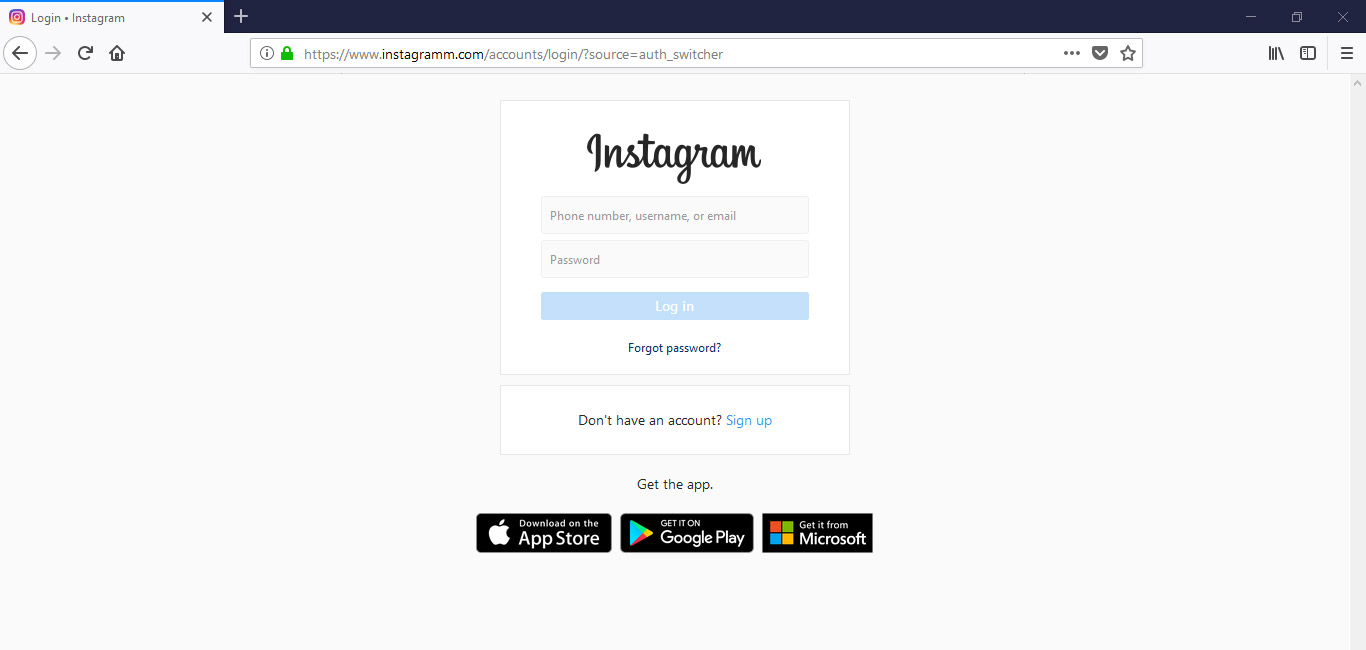

Look at the image placed above, you might not have noticed a discrepancy in the URL (https://www.instagramm.com). Spelling of the domain name, .com and forward slash is a crucial piece information to note whenever you find a login page. A legitimate URL should be https://www.instagram.com/, there shouldn’t be any change. If you notice any change, it must be a phishing page.
Instagram is a mobile app, we hardly use its web based login and hence phishing is not an easy way to hack Instagram password.
Since everybody is aware that Facebook account is enough to get started with Instagram, hacking someones Facebook account’s password leads to Instagram hacking. Therefore phishing your Facebook account password gets your Instagram account hacked.
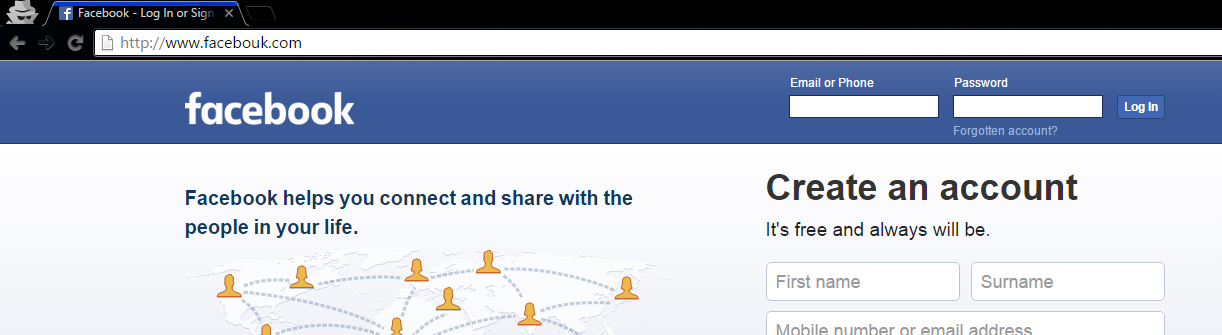

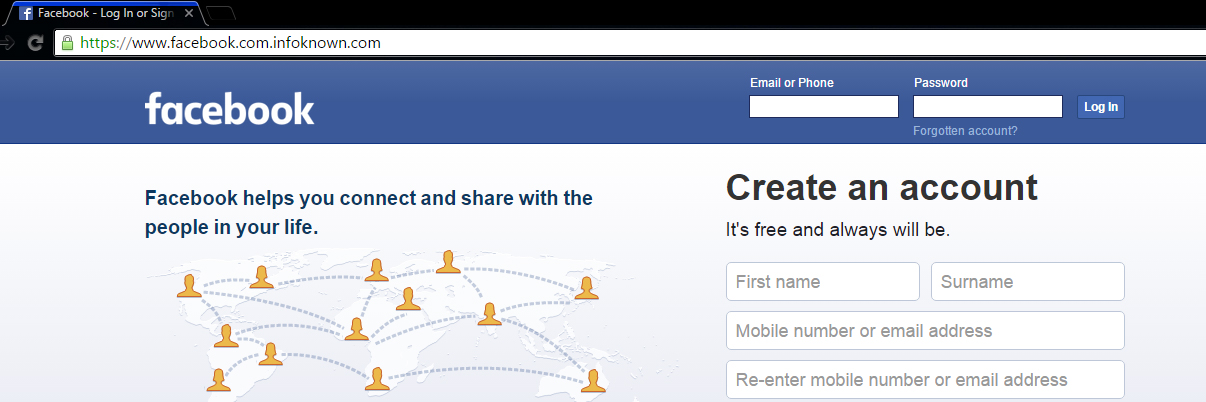

Creating a phishing page isn’t rocket science. Thousands of websites provide direct download of phishing pages. Basic programming knowledge like php / html is pretty enough for anyone to get a phishing page done. So be cautious of phishing pages.
- How to spot phishing attempts:
- Check the URL carefully: Look for misspellings or variations in the domain name (e.g.,
instagramm.cominstead ofinstagram.com). - Be wary of suspicious links: Don’t click on links in emails or messages from people you don’t know.
- Enable two-factor authentication (2FA): This adds an extra layer of security by requiring a code from your phone in addition to your password.
3. Plain password grabbing
This is one of the most common methods exploited by hackers to hack instagram accounts. We have this bad habit of using the same password for all the websites we use. I call this a bad habit because all the websites are not equally built and secured. Facebook.com might have more security mechanisms in place than a poor xyz.com. Therefore a hacker gains access to poor xyz.com’s database can hack your instagram account easily.
A password should always be hashed before storing in a database. But small and medium sized website owners store passwords in plain text and hence it is easy for a hacker to steal your all-in-all password from the vulnerable website.
How to protect yourself from hacking passwords?
- Enable two-factor authentication (2FA): This adds an extra layer of security by requiring a code from your phone in addition to your password.
- Never use a common password for day-to-day websites such as Google, Facebook, Instagram etc.
- Have two kinds of passwords.
- A strong password for important websites.
- A common easy password for other unimportant websites. Hence avoiding the need to remember multiple passwords.
4. Weak Passwords
Guessing the password through social engineering allows one to hack instagram account. It isn’t a simple task if you have a strong password.
How can we say the password is weak?
Any password that is easily guessable by a third person or someone you know is a weak password. Some common weak passwords are given below.
- Mobile Number
- Nickname / Name and Date of Birth Conjunction
- Boy Friend’s Mobile Number / Girl Friend’s Mobile Number – Most of the lovers 😛
- Girl Friend’s / Boy Friend’s Name – Most of the lovers 😛
- Boy or Girl Friend Name Combination
- Bike Number
- Unused / Old Mobile Number
- Pet Name
- Closest Person Name (can be friends too)
So if you have any one of the passwords listed above, you should change it immediately. Weak passwords are not limited to the list. We should avoid any password that is guessable.
As I have said earlier, always have two passwords. A strong password for important websites / apps and a common weak passwords for insignificant websites / apps.
5. Mobile Operating System Vulnerabilities
Android and iOS rules the world of mobile operating system and therefore vulnerabilities affecting the android and iOS can ultimately hack your mobile itself, instagram is just a part of it. These vulnerabilities are often addressed as zero day exploits. You really can’t do anything to prevent these vulnerabilities since we don’t have control over it.
Few things you can do to protect yourself
- Keep your OS updated: Install security updates as soon as they are available.
- Only install apps from official stores: Avoid sideloading apps from untrusted sources.
- Be mindful of app permissions: Don’t grant unnecessary permissions to apps.
6. Instagram zero day vulnerabilities
While rare, vulnerabilities in Instagram’s own code can be exploited by hackers. Zero days are vulnerabilities that are unknown to the software vendor i.e instagram. Black hat hackers find vulnerabilities affecting instagram in order to hack accounts.
As common users, we have limited control over vulnerabilities within the vendor’s systems. However, we can take steps to enhance our own security, such as enabling two-factor authentication. Instagram maintains a strong security posture by running a bug bounty program, which incentivizes whitehat hackers to identify and report vulnerabilities.
7. Social Engineering
Hackers may try to manipulate you into giving them your login information or access to your account. This can be through:
- Baiting: Offering something enticing (like free followers) in exchange for your login details.
- Pretexting: Creating a false scenario (like pretending to be Instagram support) to gain your trust.
- Quid pro quo: Offering a service in exchange for your information.
How to protect yourself:
- Be skeptical: Don’t trust unsolicited messages or offers that seem too good to be true.
- Verify requests: If someone claims to be from Instagram, contact Instagram support directly to confirm.
- Never share your login information: Instagram will never ask for your password.
8. Account Takeovers
Hackers might try to take over your account by:
- Guessing your password: This is why strong, unique passwords are crucial.
- Using brute-force attacks: Automated tools that try many password combinations. Even though there are rate limits for such attempts, they use methods like IP rotation to bypass it.
- Exploiting third-party app connections: Revoke access to any apps you no longer use or trust.
How to protect yourself:
- Review connected apps: Regularly check which apps have access to your Instagram account and remove any you don’t need.
- Use a strong password and 2FA: These make it much harder for hackers to gain access.
By understanding these methods and following the security tips, you can significantly reduce the risk of your Instagram account being hacked.
